Article
Best Practices in Securing DevOps
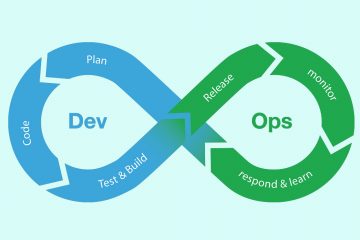
The growing demand for faster software delivery, using public cloud environments, microservices, and containers, has triggered a discussion on the role of security in the world of DevOps. At this year’s DevOps Connect at RSA Conference 2018, nearly 1,200 security professionals gathered to explore ways of embedding security into the Read more…