Ch. Muhammad Osama, an independent vulnerability researcher has discovered a Cross-Site Scripting (XSS) vulnerability in IRCCloud website www.irccloud.com, which can be exploited by an attacker to conduct Same-Site Scripting attacks.
Reference :- http://www.securityfocus.com/archive/1/486606/30/0/threaded
Same-Site Scripting :-
It’s a common and sensible practice to install records of the form “localhost. IN A 127.0.0.1” into nameserver configurations, bizarrely however, administrators often mistakenly drop the trailing dot, introducing an interesting variation of Cross-Site Scripting (XSS) I call Same-Site Scripting. The missing dot indicates that the record is not fully qualified, and thus queries of the form “localhost.example.com” are resolved. While superficially this may appear to be harmless, it does in fact allow an attacker to cheat the RFC2109 (HTTP State Management Mechanism) same origin restrictions, and therefore hijack state management data.
The result of this minor misconfiguration is that it is impossible to access sites in affected domains securely from multi-user systems. The attack is trivial, for example, from a shared UNIX system, an attacker listens on an unprivileged port[0] and then uses a typical XSS attack vector (e.g. <img src=…> in an html email) to lure a victim into requesting http://localhost.example.com:1024/example.gif, logging the request. The request will include the RFC2109 Cookie header, which could then be used to steal credentials or interact with the affected service as if they were the victim.
Another attack vector exists where a victim connects to a site from (or via) a machine that hosts another website, any XSS-like flaw or reflective web service on the hosted website can therefore be exploited in the context of the misconfigured domain. This would also affect users who connect via a shared caching http proxy machine, that also hosts an http daemon.
Proof of Concept :-
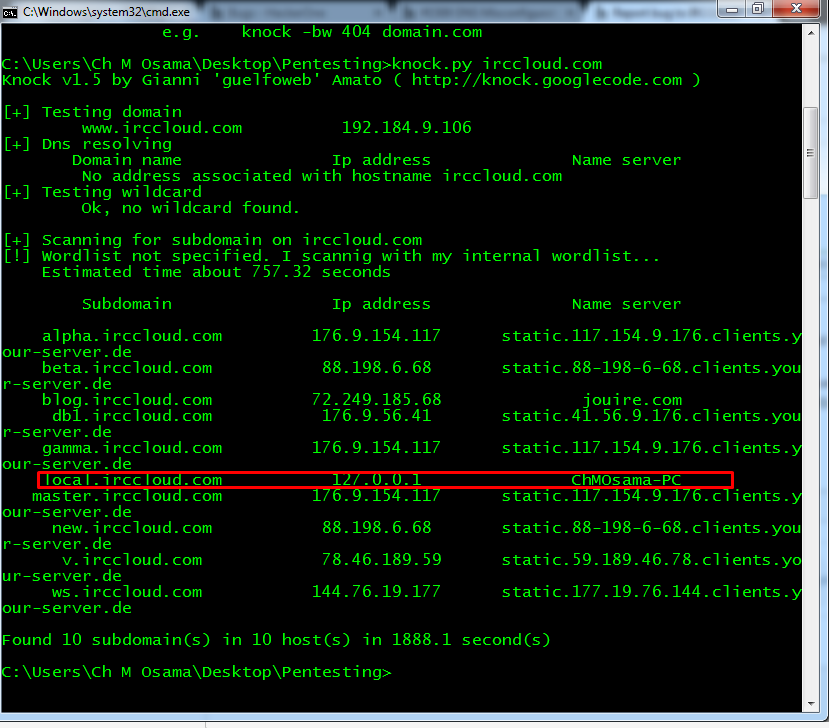
Conclusion :-
This vulnerability has been confirmed and patched by IRCCloud Security Team. I would like to thank them for their quick response to my report.
Status : Fixed!
Hall of Fame : Yes!
Bounty: No!



0 Comments